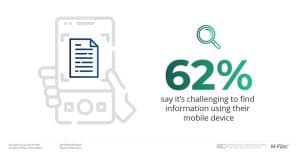
Download 100 #InformationManagement Stats that will Blow Your Mind: 62% report…
Download 100 #InformationManagement Stats that will Blow Your Mind: http://ed.gr/cr8w6 62% report that it is challenging to find the information they are looking for while



















Recent Comments