
Will Work-from-Home Lead to Shrinking Big Cities and a Suburban Explosion?
Will Work-from-Home Lead to Shrinking Big Cities and a Suburban Explosion? Source

Will Work-from-Home Lead to Shrinking Big Cities and a Suburban Explosion? Source

4 Reasons SaaS Users Love Online User Communities (and Why You’ll Love the M-Files Community) | https://ed.gr/c7jlx “In an online community, a SaaS customer can

🎄 New device? Be sure to stay safe from cyberthreats with Webroot #antivirus protection. https://wbrt.io/3smSKD1 ‘Tis the season for protecting your devices with Webroot antivirus

Infographic: Legal Tech By The Numbers | http://ed.gr/cwv9a Legal teams around the world are trying to keep pace by implementing new and exciting technologies —
The Best Way to Solve Information Management Problems of Legacy Applications Source
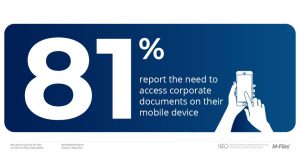
Download 100 #InformationManagement Stats that will Blow Your Mind: http://ed.gr/cr8w6 More than eight in ten (81%) respondents report the need to access corporate documents on
6 Hot Take Information Management Trends in 2021 | https://ed.gr/c7jmw “At its core, an information management system is precisely what it sounds like — a

Whitepaper: Why Professional Services Firms Should Ditch Folders and Embrace Metadata | http://ed.gr/cub37 “To stay competitive and meet market demands, professional services firms must offer

As the cyberthreat landscape continues to evolve, smart businesses are investing in #MDR solutions to boost customer protection and reduce overall costs. https://wbrt.io/3mkRAV7 Making the

For Accounting Firms, Managing Source Documents is 10x Easier with an Information Management System Source

Your Digital Transformation Success or Failure Depends on these 6 IT Department Roles Source

eBook: The Definitive Guide for Boosting Productivity with Microsoft Teams | http://ed.gr/cvysp Source

Podcast: A World without Computer Folders, Where Only What the File is Matters | https://ed.gr/cyfvc Traditional computer file storage imitates the old school file folders

All the Ways M-Files Supports HR in the New Era of Working Remotely Source

Digital Transformation at Scale: 5 Game-Changing Factors Source

From publicly announcing the program to finding an appropriate difficulty level, ensure your #phishing simulations are maximizing the results of your employee security awareness training.

Infographic: Achieving a Healthy, Future-Proof Business Consulting Firm | http://ed.gr/cvyqv Source

How Automation in the Workplace Can Help Every Type of Business Source

Download 100 #InformationManagement Stats that will Blow Your Mind: http://ed.gr/ct8jn 52% of organizations use 4 or more content systems. Source

4 Things We’ve Learned from Nearly 8 Months of Working from Home Source

This website uses cookies to ensure you get the best experience on our website. By using our website you agree to our Privacy Policy.
Recent Comments